Container Support : Synology VS QNAP
One of the ways to add applications to your NAS is by running containers on the NAS itself. Both QNAP and Synology have user-friendly interfaces that allow you to create, manage, and run your containers. Synology calls this feature "Container Manager," while QNAP names it "Container Station."
These two solutions share more similarities than differences. Lets look at the little difference they have .
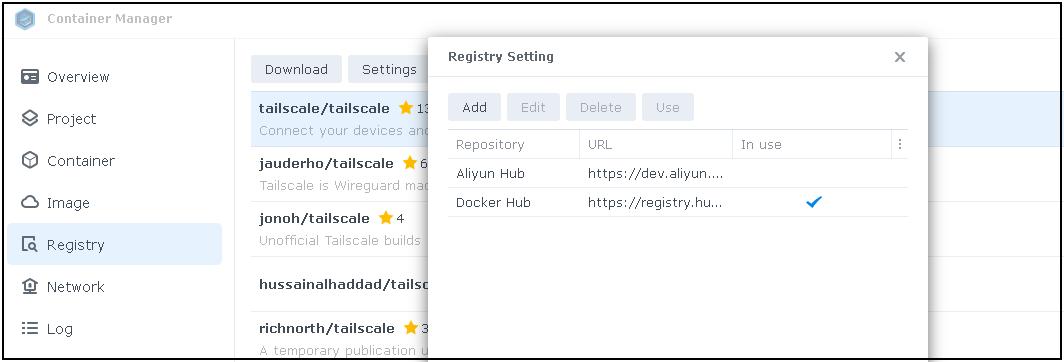
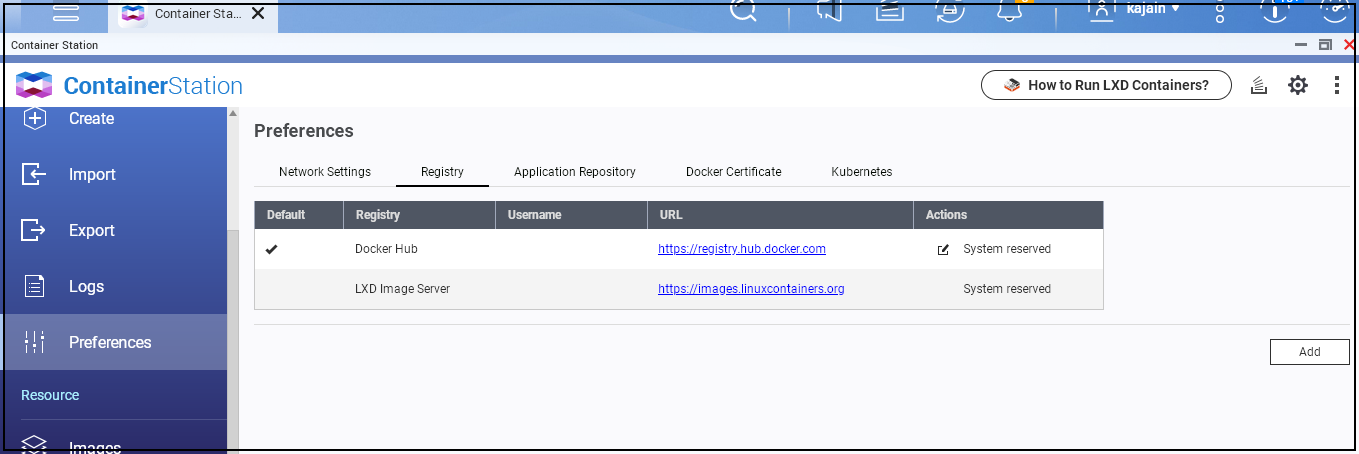
QNAP Supports LXD, Docker and Kata. Synology only Docker
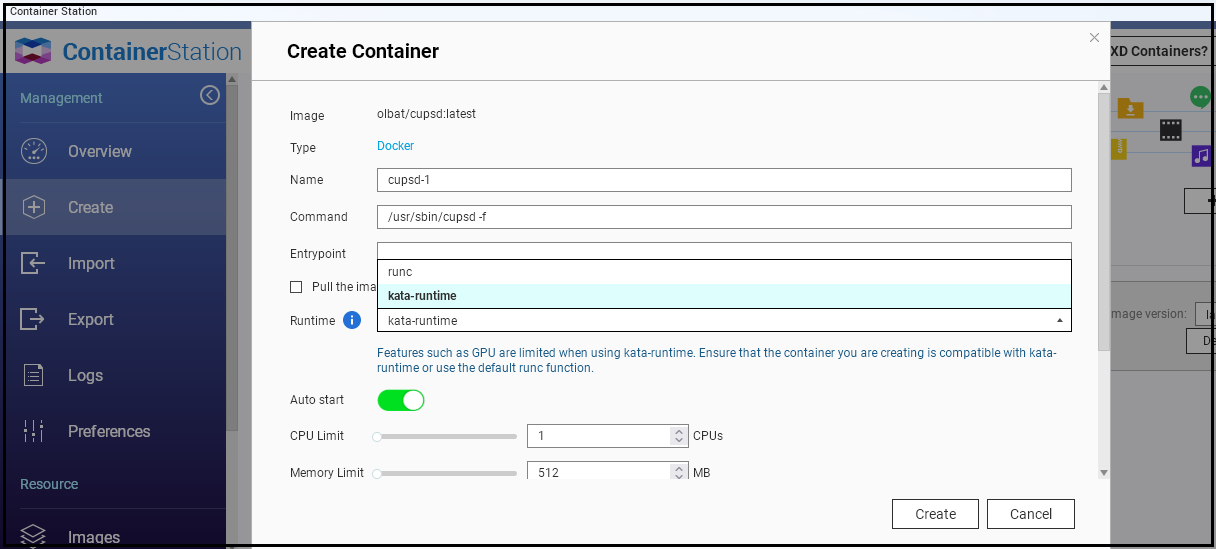
Docker is the most popular container platform , yet it's not the only one . Thre are many other Alternatives notably LXC/LXD which allow complete OS execution as a container, and Kata which offers better isolation through VM . QNAP supports Docker, LXD, and Kata.
There are many articles that detail differences among these platforms, but it simplifies to this: If you require an entire OS like Ubuntu as a container, opt for LXD. For greater isolation beyond standard containers, select Kata runtime . for everything else, use Docker .
On QNAP you can use all these, while Synology's support is limited to Docker.
Synology Offers Granular control over runtime privileges, QNAP has only a privileged mode
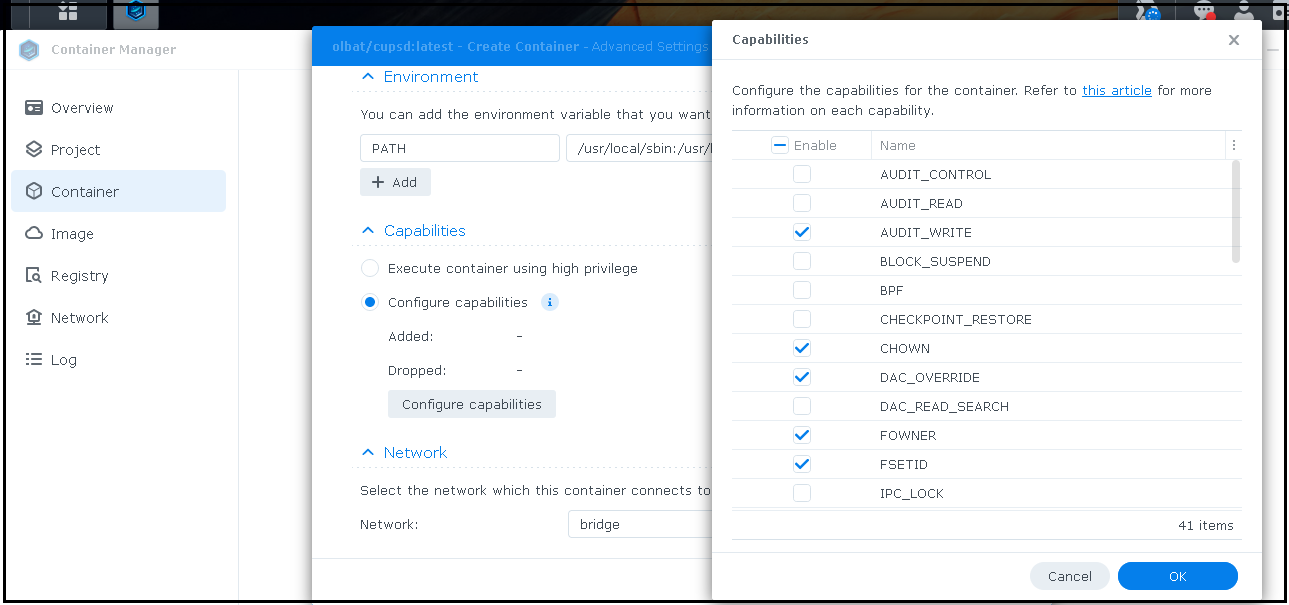
Docker has a "privileged" mode, granting containers access to all host devices. Both QNAP and Synology let the user enable this privilege mode with a simple click . Synology goes a step further by supporting the 41 Linux capabilities, offering finer control over privileges.
List of all the Linux capability options Synology Supports.
AUDIT_WRITE Write records to kernel auditing log.
CHOWN Make arbitrary changes to file UIDs and GIDs (see chown(2)).
DAC_OVERRIDE Bypass file read, write, and execute permission checks.
FOWNER Bypass permission checks on operations that normally require the file system UID of the process to match the UID of the file.
FSETID Don't clear set-user-ID and set-group-ID permission bits when a file is modified.
KILL Bypass permission checks for sending signals.
MKNOD Create special files using mknod(2).
NET_BIND_SERVICE Bind a socket to internet domain privileged ports (port numbers less than 1024).
NET_RAW Use RAW and PACKET sockets.
SETFCAP Set file capabilities.
SETGID Make arbitrary manipulations of process GIDs and supplementary GID list.
SETPCAP Modify process capabilities.
SETUID Make arbitrary manipulations of process UIDs.
SYS_CHROOT Use chroot(2), change root directory.
AUDIT_CONTROL Enable and disable kernel auditing; change auditing filter rules; retrieve auditing status and filtering rules.
AUDIT_READ Allow reading the audit log via multicast netlink socket.
BLOCK_SUSPEND Allow preventing system suspends.
BPF Allow creating BPF maps, loading BPF Type Format (BTF) data, retrieve JITed code of BPF programs, and more.
CHECKPOINT_RESTORE Allow checkpoint/restore related operations. Introduced in kernel 5.9.
DAC_READ_SEARCH Bypass file read permission checks and directory read and execute permission checks.
IPC_LOCK Lock memory (mlock(2), mlockall(2), mmap(2), shmctl(2)).
IPC_OWNER Bypass permission checks for operations on System V IPC objects.
LEASE Establish leases on arbitrary files (see fcntl(2)).
LINUX_IMMUTABLE Set the FS_APPEND_FL and FS_IMMUTABLE_FL i-node flags.
MAC_ADMIN Allow MAC configuration or state changes. Implemented for the Smack LSM.
MAC_OVERRIDE Override Mandatory Access Control (MAC). Implemented for the Smack Linux Security Module (LSM).
NET_ADMIN Perform various network-related operations.
NET_BROADCAST Make socket broadcasts, and listen to multicasts.
PERFMON Allow system performance and observability privileged operations using perf_events, i915_perf and other kernel subsystems
SYS_ADMIN Perform a range of system administration operations.
SYS_BOOT Use reboot(2) and kexec_load(2), reboot and load a new kernel for later execution.
SYS_MODULE Load and unload kernel modules.
SYS_NICE Raise process nice value (nice(2), setpriority(2)) and change the nice value for arbitrary processes.
SYS_PACCT Use acct(2), switch process accounting on or off.
SYS_PTRACE Trace arbitrary processes using ptrace(2).
SYS_RAWIO Perform I/O port operations (iopl(2) and ioperm(2)).
SYS_RESOURCE Override resource Limits.
SYS_TIME Set system clock (settimeofday(2), stime(2), adjtimex(2)); set real-time (hardware) clock.
SYS_TTY_CONFIG Use vhangup(2); employ various privileged ioctl(2) operations on virtual terminals.
SYSLOG Perform privileged syslog(2) operations.
WAKE_ALARM Trigger something that will wake up the system.List of All Linux Capabilities Options that Synology Supports
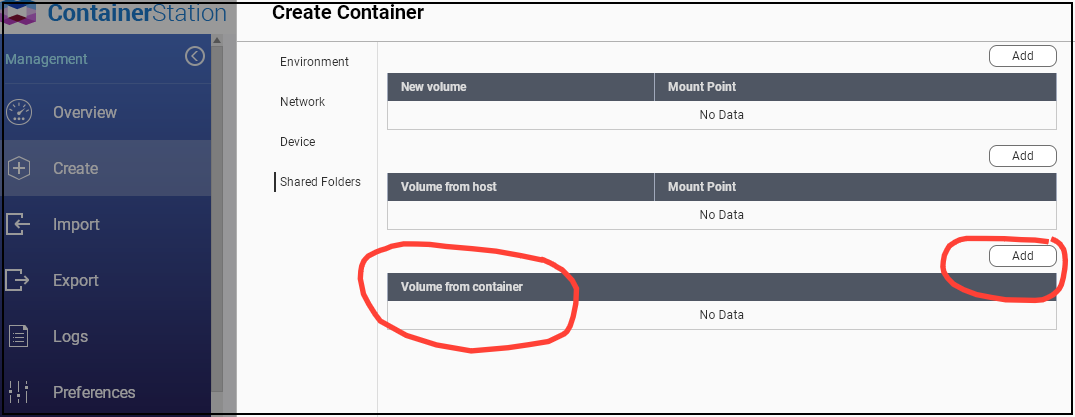
QNAP lets you access container volumes from host easily, Synology Doesnt
QNAP offers the flexibility of mapping volumes both from the host to the container and vice versa. However, with Synology, you can only mount a host volume to a container. This means that if you need to make changes to container files, QNAP provides a more convenient option.
Summary
Here is TL;DR of the entire article
- QNAP supports Docker, LXD, and Kata runtime, whereas Synology only supports Docker. This translates to quicker performance for full Linux OS on QNAP and more secure, isolated containers compared to standard Docker containers on Synology.
- QNAP supports only privileged mode, while Synology offers finer control through Linux capability options , in addition to privileged mode
- QNAP supports container volume mapping to the host, useful for modifying configuration files within the container for example.
| QNAP Container Station | Synology Container Manager | |
| Support | Docker, LXD, Kata | Docker |
| Repository | Docker Hub, LXD image, custom add | Docker Hub, custom add |
| Auto Start | Yes | Yes |
| Resourse Limitation | Yes | Yes |
| Network Mode | Bridge, Host,NAT | Bridge, host ( NAT port forward) |
| Host Volume mapped to Container | Yes | Yes |
| Container Volume Mapped to host | Yes | No |
| Privileged Mode | Yes | Yes |
| Granulated Runtime Control | No | Yes |
| Terminal Access | Yes | Yes |
| Run Stack | Yes | Yes |